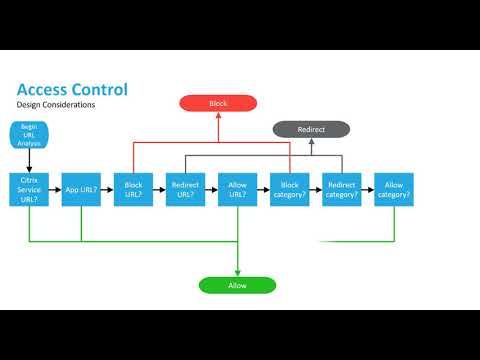
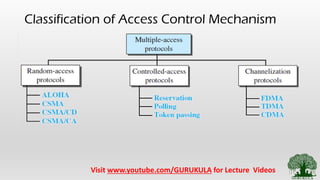
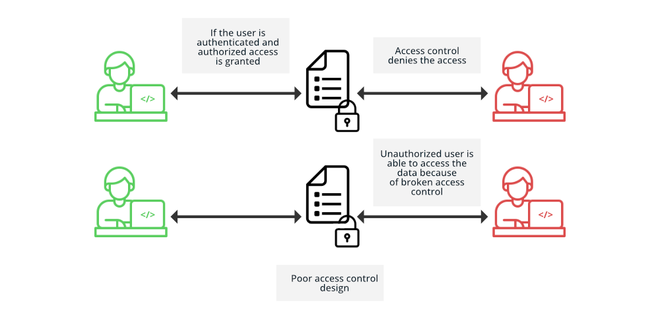
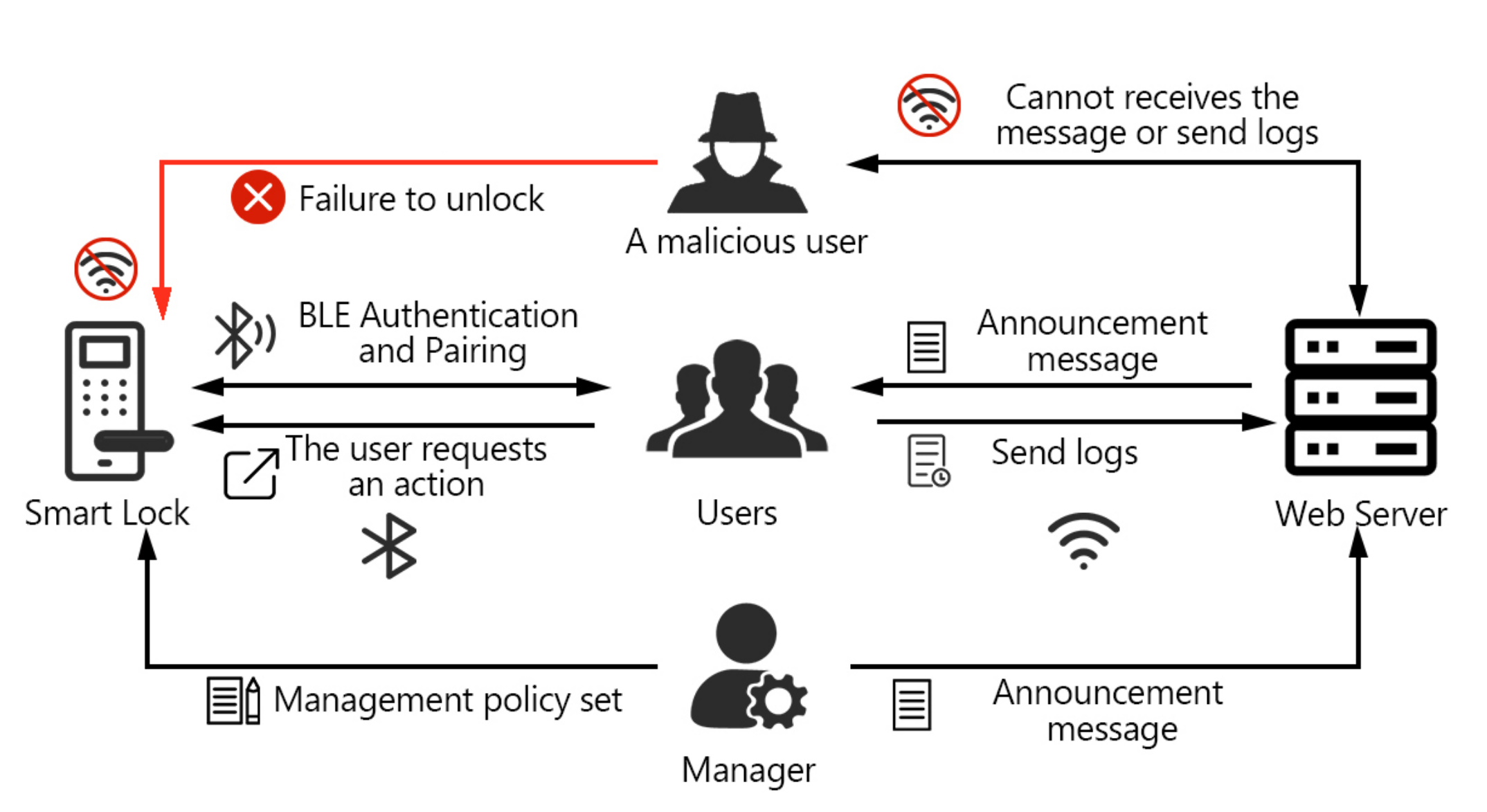
Architecture Of Access Control Mechanism In Run Time Change Management | Download Scientific Diagram

Discretionary and Non-Discretionary Access Control Policies by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu

A decentralized access control mechanism using authorization certificate for distributed file systems | Semantic Scholar

Figure 1 from A decentralized access control mechanism using authorization certificate for distributed file systems | Semantic Scholar
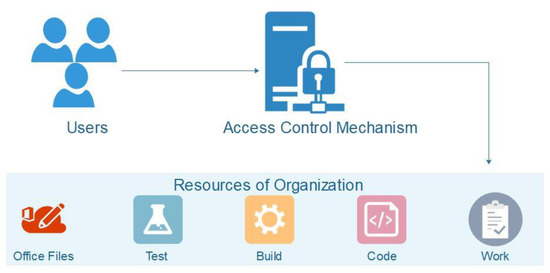
Symmetry | Free Full-Text | Permission-Based Separation of Duty in Dynamic Role-Based Access Control Model
![PDF] An Authorization Mechanism for Access Control of Resources in the Web Services Paradigm | Semantic Scholar PDF] An Authorization Mechanism for Access Control of Resources in the Web Services Paradigm | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/45dbf0db8d7af588bca0e0ecf32fe304f6a3b3fd/3-Figure1-1.png)