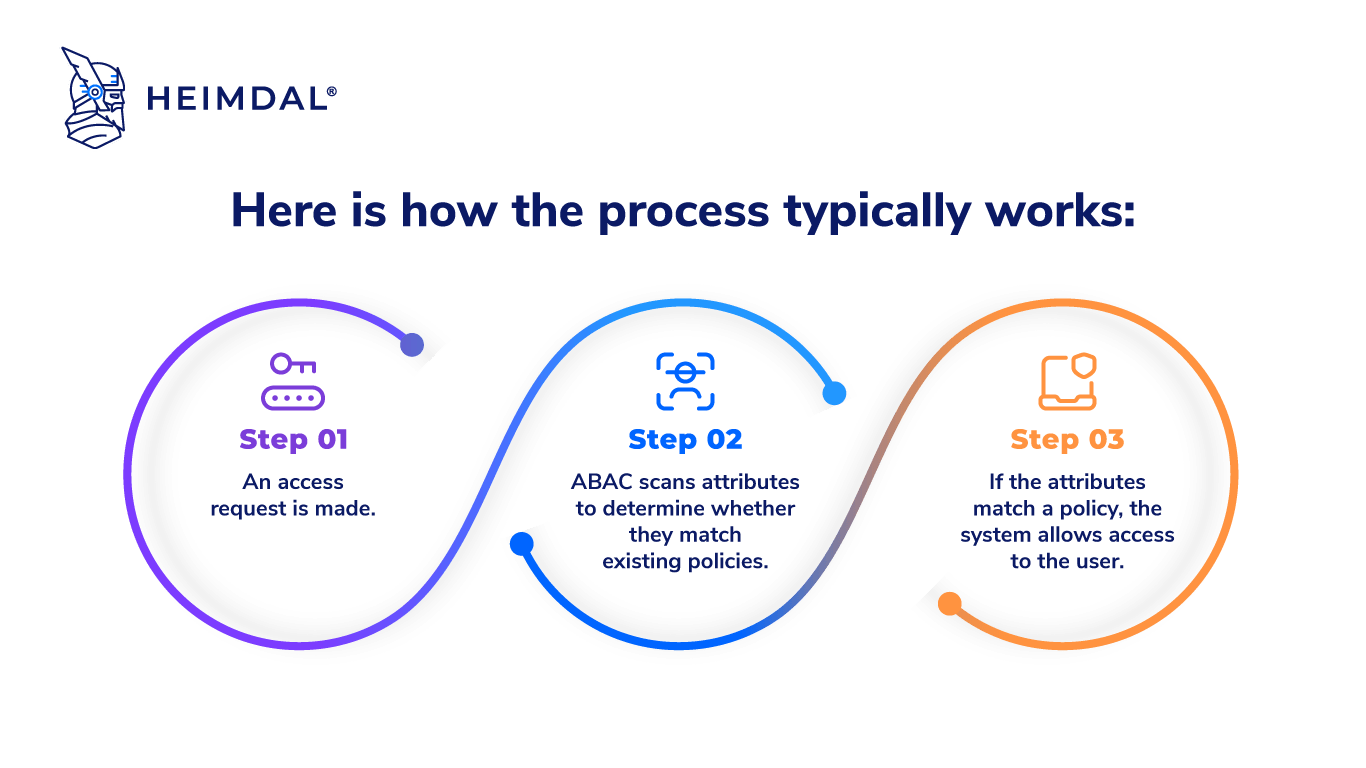
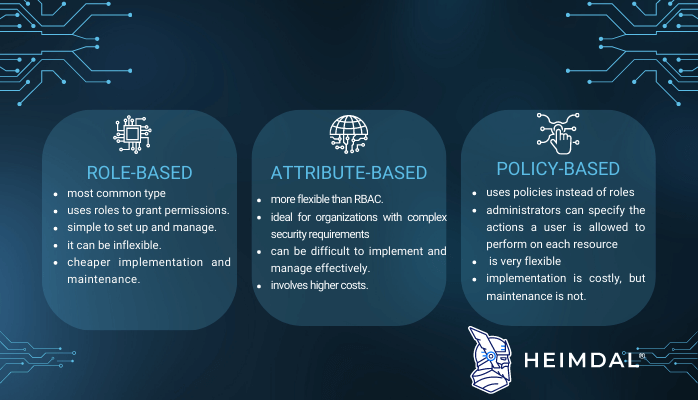
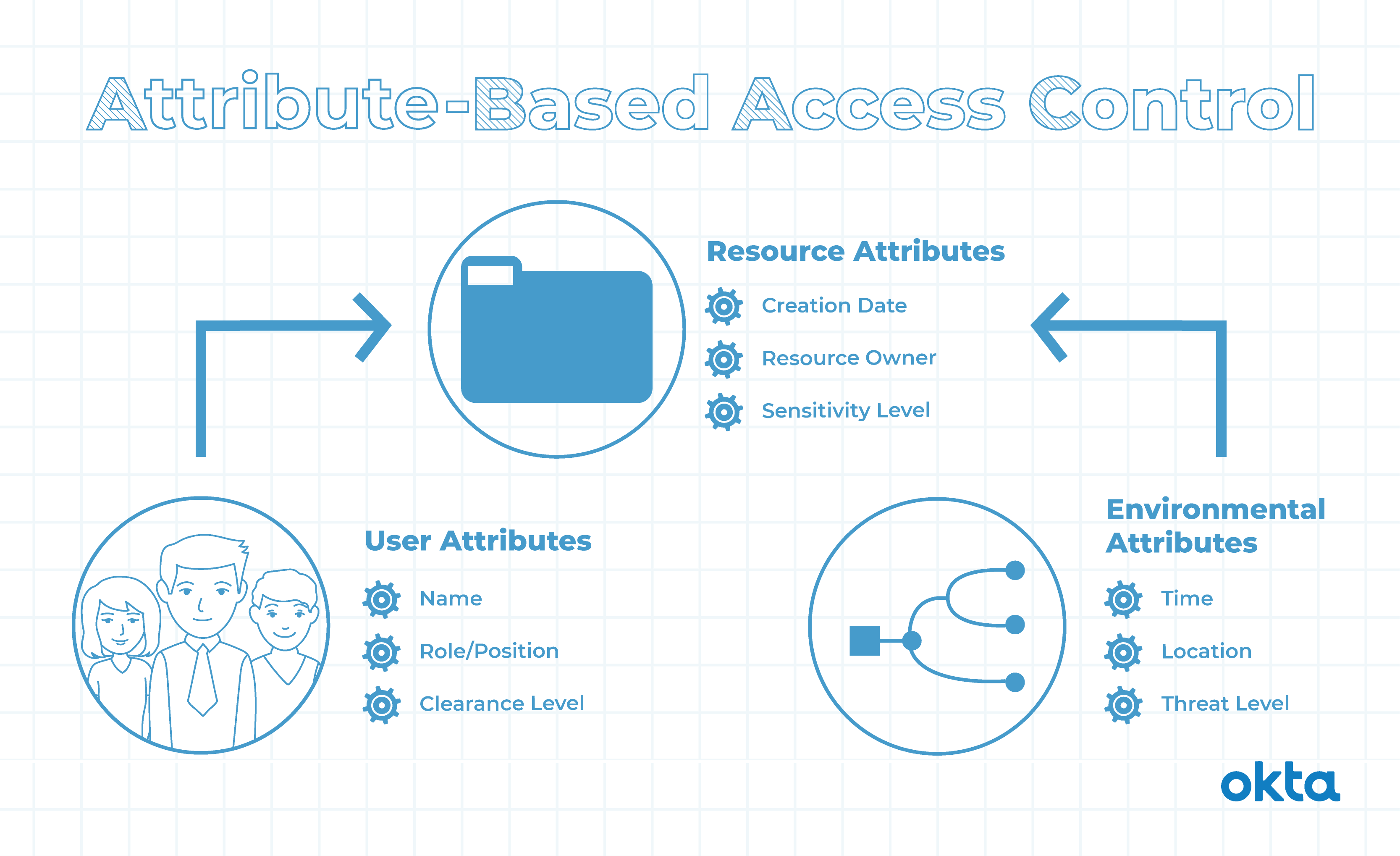
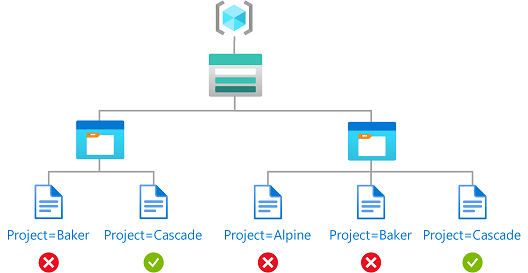
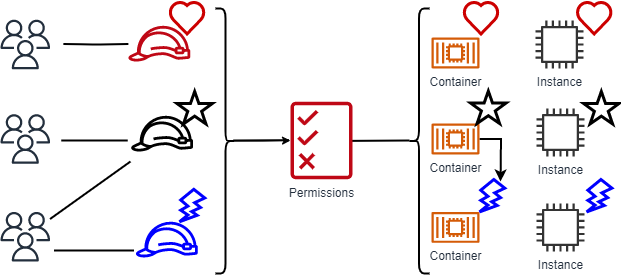
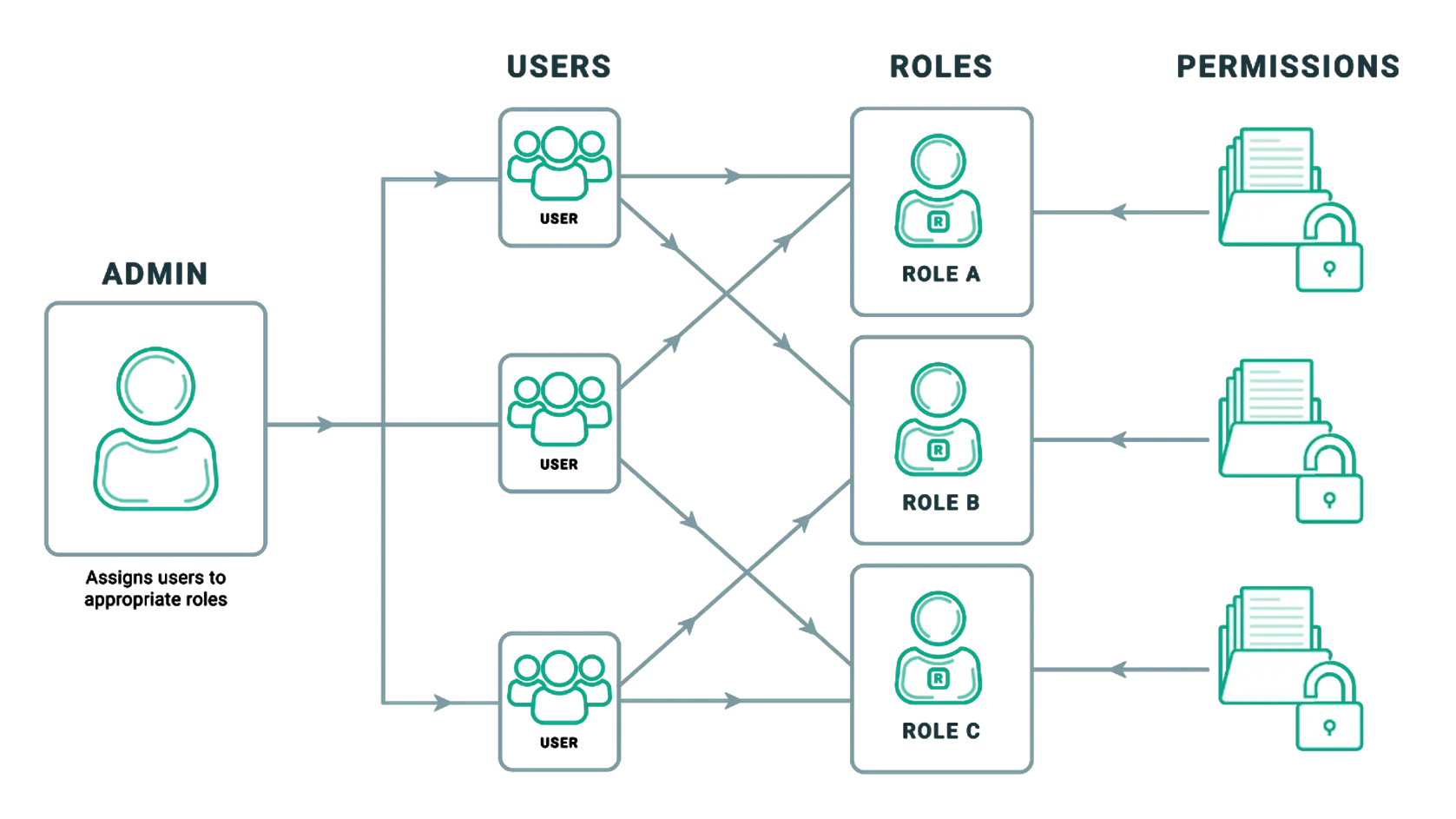
Attribute Based Access Control (ABAC) in a microservices architecture for lists of resources - Stack Overflow

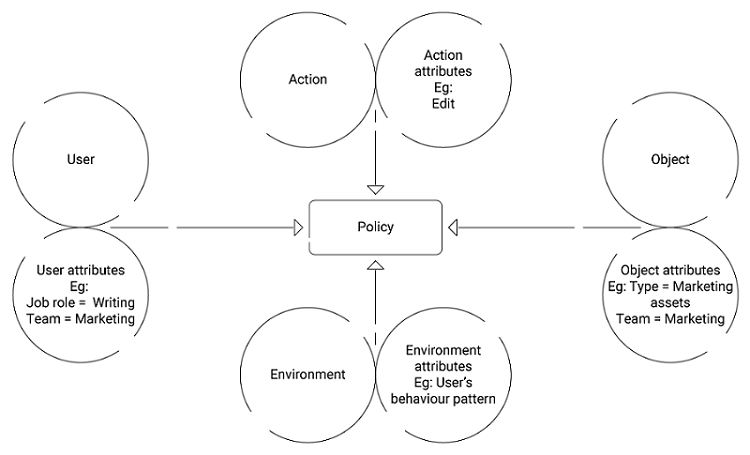
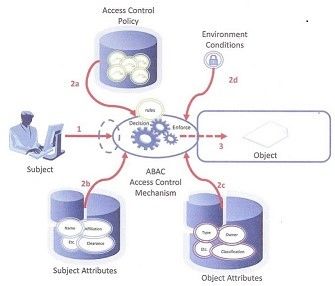
Figure 4 from Guide to Attribute Based Access Control (ABAC) Definition and Considerations | Semantic Scholar
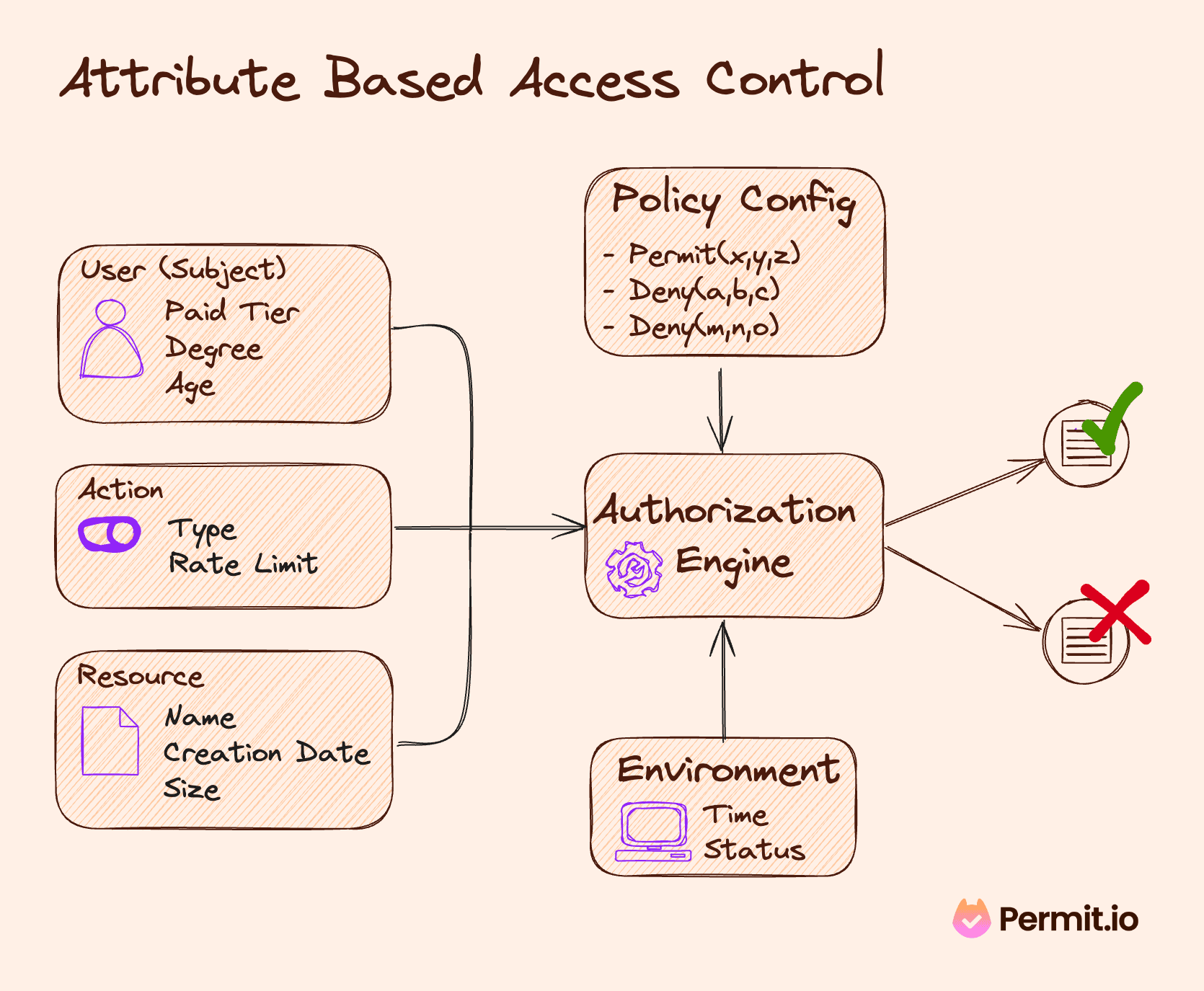
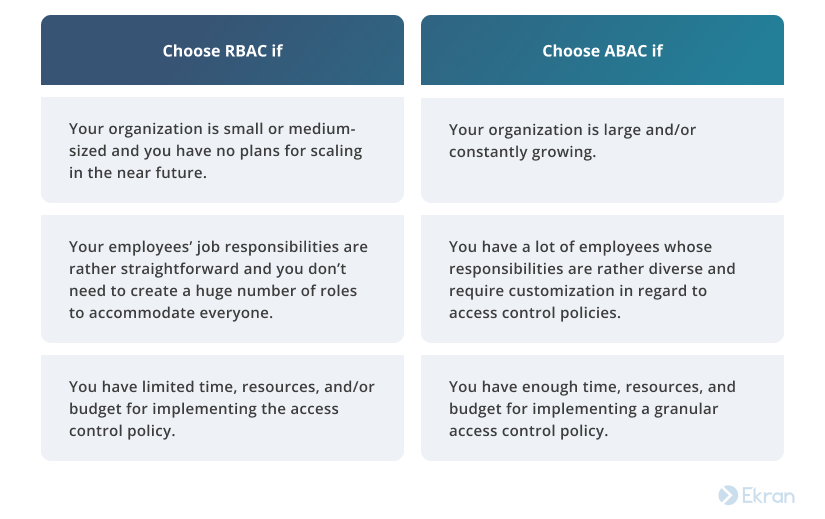
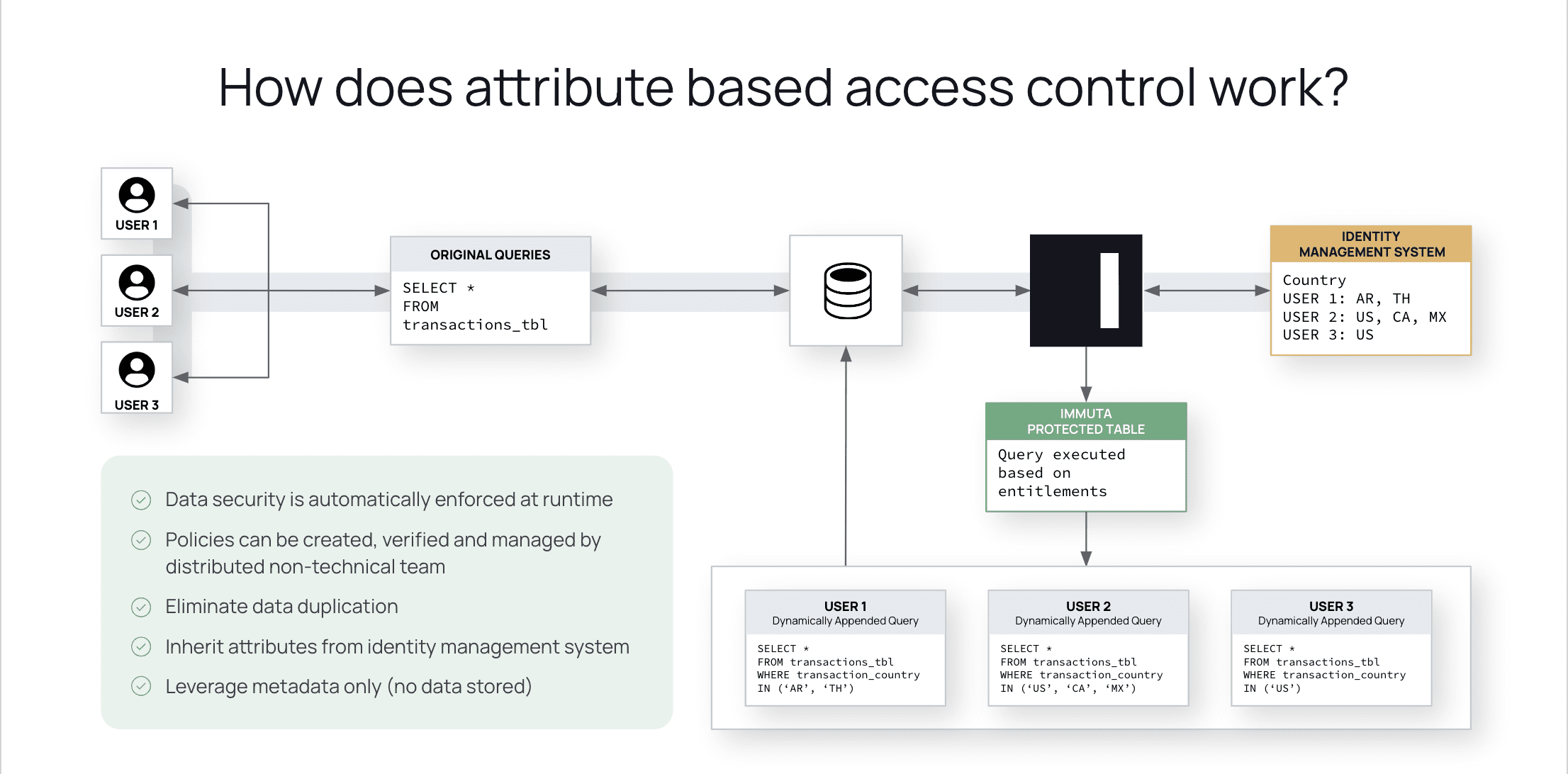
DZone: Why Attribute-Based Access Control - The Evolution from RBAC to ABAC in Data Access Control - Axiomatics